May 2, 2022 by Arun vats
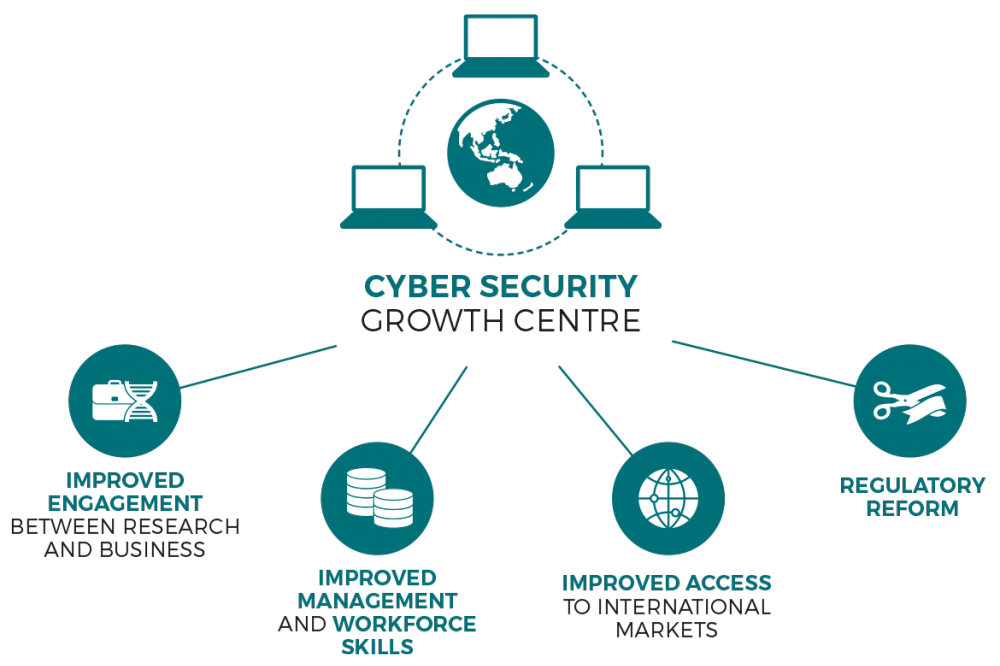
CYBER SECURITY
"Cyber security is the body of technology, process & practices designed to secure networks, devices, programs, and data from cyber-attack, damage, or unauthorized access."
WOULD YOU LIKE TO DISCUSS SOMETHING WITH TEAM WDGROUP? DROP IN YOUR CONTACT DETAILS SO WE CAN GET IN TOUCH WITH YOU.